Abstract
In the past few decades, crime has increasingly moved into the informational sphere from its historical base in the physical world. Even to our modern equivalent—credit and debit cards—robbery has changed since the days when goods were delivered by stagecoach to stay up. This is because while crime does persist forever, its patterns are constantly changing. Credit card data theft, web-based assaults, data breaches, denial of service, hacking, virus dissemination, logic bombs, phishing, email bombing and spamming, web jacking, cyberstalking, data diddling, salami slicing attacks, software piracy, etc. are now recognized risks. This research paper explores the shifting landscape of crime from the physical to the informational domain, focusing on the myriad cyber threats prevalent today. With a global perspective on cybercrime legislation, the study highlights the absence of formal laws protecting financial data in Bangladesh, despite constitutional safeguards for citizen privacy. Delving into the challenges of enforcing legislation, the research assesses the effectiveness of current laws against cybercrime and examines the dissonance between legal frameworks and practical implementation. Emphasizing the government's pivotal role in addressing emerging economic threats, the study draws insights from a comprehensive analysis of available data in papers, journals, and reports.
Keywords: financial organizations, hacking, internet banking.
1. Introduction
In the dynamic landscape of the 21st century, the evolution of crime has taken an unprecedented turn, transcending its conventional boundaries into the vast realm of cyberspace. The past few decades have witnessed a remarkable shift from physical-world criminal activities to a sophisticated realm where information is the prized commodity. Even the infamous act of robbery has morphed into a digital menace, preying on credit and debit card transactions rather than traditional stagecoach deliveries.
As technology advances, so does the nature of criminality. From credit card data theft to web-based assaults, the array of cyber threats has expanded to include data breaches, denial of service attacks, hacking, virus dissemination, logic bombs, phishing, email bombing, spamming, web jacking, cyberstalking, data diddling, salami slicing attacks, and software piracy. These emerging risks underscore the urgency for robust legal frameworks to combat cybercrime effectively.
While global awareness of cyber threats has prompted legislative action, the response across nations remains uneven. According to the United Nations Conference on Trade and Development (UNCTAD), out of 195 nations, only 156 have enacted specific cybercrime legislation to safeguard and protect data. Notably, some Asian countries, such as China, Vietnam, India, and Singapore, have proactively adopted specialized laws to govern cyber delinquencies. However, most nations, including Bangladesh, rely on general laws that focus on safeguarding personal information, governmental institution data, and electronic commerce-related information.
Despite being a signatory to the International Covenant on Civil and Political Rights (ICCPR) of 1966, Bangladesh grapples with a legislative gap in addressing cyber threats to its financial sectors and the protection of customer data. While Article 17 of the ICCPR prohibits arbitrary interference with privacy, and Article 43(B) of the Constitution of Bangladesh safeguards citizens' privacy in correspondence and communication, there is a glaring absence of formal laws specifically addressing the intricacies of cybercrime.
Within the financial sector, Bangladesh faces imminent challenges. Sixty-one scheduled banks, operating under the full control and supervision of Bangladesh Bank, find themselves in a precarious situation due to the inadequacy of the current legal framework. Enshrined in the Bank Company Act of 1991 and the Bangladesh Bank Order of 1972, this framework falls short in addressing the burgeoning economic threats posed by cybercrime. A study by the Bangladesh Institute of Bank Management (BIBM) has underscored this vulnerability, revealing that 52% of banks in Bangladesh are currently at high risk of falling victim to cyber-attacks.
The objective of this research is to delve into the intricacies of curbing cybercrime in Bangladesh. It aims to scrutinize the challenges in enforcing legislation, evaluate the effectiveness of existing laws in preventing cybercrime, and unravel the discrepancies between legal provisions and practical implementation. Drawing on a comprehensive range of data sources, including academic papers, journals, and various reports, this study endeavors to shed light on the multifaceted landscape of cyber threats faced by Bangladesh and propose informed recommendations to fortify its defenses against this evolving menace.
2. Materials and Methods
The research has been conducted by deductive research methodology where existing laws related to the protection of cybercrime have been gathered and the problems during implementation have been analyzed through case studies and some secondary research. The paper will show the current situation of the economic organizations of Bangladesh. Existing information and data made available through numerous sources are gathered for this study, compared, and then analyzed to yield logical conclusions and a solution to the research topic. The primary sources are white papers, government records, academic publications, journals, print media, statistical data banks plus historical records. Since a solid collection of data already exists in a documented form, a secondary method of data gathering, and analysis is used in this instance. The subject matter and the time constraint may make doing direct study an impractical endeavor. Here, a historical viewpoint is used to uncover records of prior cybercrime scenarios and compile a list of preventative measures to create a platform that is anti-cybercrime. The scope of the research is to study solutions for cyber-attacks on Bangladesh's financial sector only, thereby narrowing the focus to bank cyber-crime cases in Bangladesh and identifying the types of cyber-attacks that the banks are likely to encounter every day.
3. Objectives of the Study
General objective: The broad objective of the study is to identify the prospects and challenges of Cybercrime in the Financial Sector of Bangladesh.
Specific objectives:
4. Results and Discussion/ Implication
The banking industry of Bangladesh has changed the way of providing services to their customers and processing of information in recent years. Electronic banking is becoming more popular and enhancing the adoption of financial inclusion. Security of Information for financial institutions has therefore gained much importance and it is vital for us to ensure that the risks are properly identified and managed. A financial institution (FI) is a company engaged in the business of dealing with financial and monetary transactions such as deposits, loans, investments, and currency exchange. Financial institutions include a broad range of business operations within the financial services sector, including banks, insurance companies, brokerage firms, and investment dealers.There are 61 scheduled banks in Bangladesh established under the Bangladesh Bank Order, of 1972 and the Bank Company Act, of 1991. Amongst them are 43 private commercial banks, 10 Islamic Shariah-based Private Commercial Banks, and so on. There are also 5 nonscheduled banks. To protect internet security this bank must follow the Guidelines on ICT Security for Banks and Non-Bank Financial Institutions published in May 2015 by The Bangladesh Bank.
4.1.Types of financial Institutions:
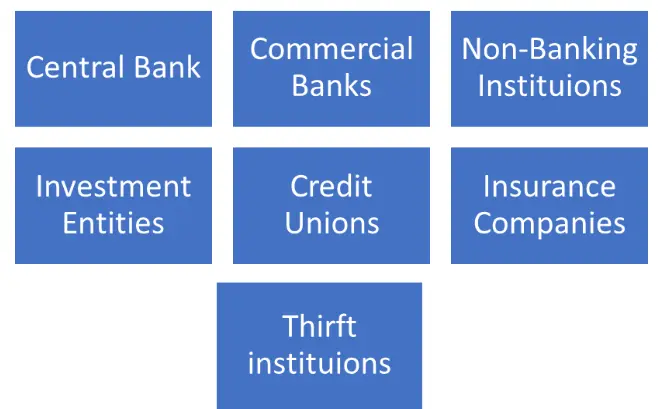
4.2.Functions of Financial Institutions:
a) Banking service
b) Investment advice
c) Regulate money supply.
d) Manage financial risks.
e) Capital information.
f) Catalyze economic growth.
g) Easy fund transfer
4.3 Outline on Present Financial Organizations:
According to the Bangladesh Bank Order 1972 currently we found 61 scheduled bank and 5 nonscheduled banks. Bangladesh bank operates this financial organization under its supervision and full control of Bangladesh Bank Order, 1972 and Bank Company Act, 1991.For smooth banking system these scheduled Banks are categorized into following types:
The threats countered by cyber-security are three-fold:
4.5 Incidents of Cyber Attack in Bangladesh:

4.3.1 Scheduled Bank:
The Banks that are enlisted or included in the scheme of the central bank. Currently in Bangladesh there are total sixty-one scheduled beneath the following criteria.
a. State Owned Commercial Banks (SOCBs): There are six SOCBs which are fully or majorly owned by the Government of Bangladesh.
b. Specialized Banks (SDBs): Three specialized banks are now operating which were established for specific objectives like agricultural or industrial development. These banks are also fully or majorly owned by the Government of Bangladesh.
c. Private Commercial Banks (PCBs): There are forty-three private commercial banks which are majorly owned by individuals/the private entities. PCBs can be categorized into two groups:
d. Foreign Commercial Banks (FCBs): Nine FCBs are operating in Bangladesh as the branches of the banks which are incorporated in abroad.
4.3.2. Non-scheduled Bank:
Non- Scheduled banks are those banks which are not included in the list of central banks, and they do not get the privileges of clearing system and re discounting of bill. Followings are the existing five non-scheduled banks in Bangladesh which are:
a. Ansar VDP Unnayan Bank,
b. Karmashangosthan Bank,
c. Grameen Bank,
d. Jubilee Bank,
e. Palli Sanchay Bank.
1.3.3. FIs:
Non-Bank Financial Institutions (FIs) are those types of financial institutions which are regulated under Financial Institution Act, 1993 and controlled by Bangladesh Bank. Now, thirty-five FIs are operating in Bangladesh while the maiden one was established in 1981. Out of the total, two is fully government owned, one is the subsidiary of a SOCB, nineteen were initiated by private domestic initiative and thirteen were initiated by joint venture initiative.
4.4 Types of Cyber-Attacks in Financial Sector:
A cyberattack is any intentional effort to steal, expose, alter, disable, or destroy data, applications, or other assets through unauthorized access to a network, computer system or digital device. The attack can be caused by some common methods such as: Malware like Virus, Trojans, Spyware, Ransomware, Adware, etc. Besides this Botnets, SQL injection, Phishing, Vishing, Smishing, DNS Phishing, Farming, Man-inthe-middle attack, Denial-ofservice attack, etc. are mentionable cyber-attack. Dridex malware (December 2019), Romance scams (February 2020), Emoted malware (late 2019), etc. are some latest cyber threats of the world. The methods have been categories in some criteria as:
a. Removable Media: Cyber criminals or hackers can achieve unauthorized access to corporate data and systems through removable media, such as flash drives and Universal Serial Bus (USB) drives to infect removable drives with viruses
b. Brute-force Attacks: In this method hackers use trial and error to guess encryption keys, user logins, or find hidden webpages. They use brute force to go through all possible combinations to make a correct guess.
c. Web or Email Attacks: It is the most common threat path. Hackers typically use email to spread phishing campaigns and links to spoofed websites, which enable them to steal users’ login credentials.
d. Unauthorized Use of System Privileges: These types of cyberattacks occur financial organizations when hackers gain unauthorized access to their systems. They typically exploit a weakness, such as an unused account, then create backdoors into compromised systems finally they got access to the network, steal data, and potentially increase their privileges to gain access to more sensitive information.
e. Loss or Theft of Devices: The loss or theft of devices continues to be an issue for financial institutions. In the wrong hands, these devices can leak sensitive corporate information to hackers, who may still be able to access data even if the device has a strong password.
f. Web Application Attacks: Web-facing applications are popular targets for cyber criminals. Hackers typically use denial-of-service (DoS) attacks and more sophisticated attack vectors like buffer overflows, cookie poisoning, cross-site scripting (XSS), and Structured Query Language injection (SQLi) to steal critical data and gain access to wider networks.
g. Malware: Hackers use malicious software (malware) to launch various financial services cyberattack types. Malware enables an attacker to gain access to a network and any connected device, steal data, and damage systems. Malware comes in several forms, including spyware, Trojans, viruses, and worms, and typically results in:
h. Ransomware: Ransomware is also a form of malware where attackers use to hold their victims’ data hostage in exchange for the payment of a fee. Ransomware attacks often start with phishing emails containing malicious attachments.
i. Distributed Denial-of-service Attacks (DDoS): Distributed DoS (DDoS) attacks occur when a cybercriminal floods a company’s server with internet traffic. This prevents users from accessing services and affects the performance of the organization’s websites. DDoS attacks are often carried out by disgruntled employees, hacktivists, or hackers wanting to show off their prowess by exploiting a weakness.
j. Spam and Phishing: Email-based attacks like spam and phishing remain one of the most popular cyberattack types on financial institutions. Attackers use phishing campaigns to steal sensitive data like account logins, banking account details, and credit card information. Spam and phishing attacks are often financially motivated and can also result in significant data loss.
k. Corporate Account Takeover: Corporate account takeovers pose a significant threat to financial institutions. They involve an attacker taking control of an organization’s bank account to steal employees’ passwords and other credentials.
l. Automated Teller Machine Cash Out: Automated teller machines (ATMs) are profitable targets for cyber criminals. Attackers can cash out an ATM by using malware to infect and manipulate the machine.
m. TCP/IP Spoofing: One of the basic types of Internet coverage is TCP / IP satirizing. In IP caricaturing, an aggressor improves unauthorized access to a PC or system by causing it to give the impression that the machine's IP address has originated from a vindictive message entrusted to the machine by ―parody. IP address parodying is the technique by which the assailant can send bundles on a scheme without the firewall structure being caught and obstructed. For most of the channels, these firewall frameworks were any external IP address that tried to talk to it. Notwithstanding, utilizing IP caricaturing, the aggressor can veil its personality by making their IP address to seem to originate from the interior system, in this manner making the firewall unfit to capture it, thus parcels can undoubtedly move by the assailants.
The threats countered by cyber-security are three-fold:
4.5 Incidents of Cyber Attack in Bangladesh:
The banking sector is the heart of a healthy economy. This is especially true for a developing country like Bangladesh. Since independence, this sector has kept the wheel of the economy moving forward. So, it's natural that any disruption in the sector will lead to effects in the economy of the country. In this context, cyber security in the banking sector is a crying issue in recent times especially after the Bangladesh bank Heist in 2016. The BIBM study has found that most of the attacks, 24% to be precise, come from China, followed by Russia 12%, and North Korea 13%. Bangladeshi banks experience 72% of total online frauds through the SWIFT system in terms of value, while 20% of the frauds are executed through banking software, and the rest through other digital channels such as mobile banking, internet banking clearing, and ATM, according to the study. In the last couple of years, several security breaches had happened in the banking sector of Bangladesh and some of those are shown in the following table- 1
| Time of occurrence | Incidents |
| January 06, 2013 | Islami Bank Bangladesh site was hacked by Human Mind Cracker |
| 2015 | Accounts of a private bank were hacked, and money was withdrawn |
| December 02, 2015 | Sonali Bank’s network security was broken, and control was taken by the hacker for several hours |
| February 2016 | Attacks in six ATM booths of three commercial banks |
| February 2016 | Hackers stole $101 million from Bangladesh Bank |
Table-2: Major Scams, Irregularities and Heists in Banks of Bangladesh over the years
| Bank / Institution Involved | Scam | Measures |
| Sonali, Janata, NCC, Mercantile and Dhaka Bank (2008-2011) | A bank loan of BDT 4.89 crores with fake land documents. (Dhaka Tribune, 28th August,2013) | The ACC submitted cases against Sonali Bank, Fahim Attire Limited and some people on 1st August 2013; returned to Sonali Bank after the inquiry BDT 1 crore (making the complete BDT 4.89 from the original 5.89 crores). (Dhaka Tribune, August 2, 2013; New Age, August 2, 2013; Daily Star, August 2, 2013) |
| BASIC Bank (2009-2013) | Misappropriation of BDT 4,500crores through forged companies and doubtful accounts. (The Daily Star, 28th June 2013) | The ACC lodged 56 cases in September 2015 against 120 individuals charged with swindling. (Bangladesh New Age,13th August 2018) |
| Sonali Bank (2010-2012) | Hall Mark and some other businesses stole BDT 3,547 crores. (The Daily Star,14th August, 2012) | The ACC lodged 11 cases against 27 individuals in October 2012, including the Chairman of the Hallmark Group and the 20 former and present representatives of Sonali Bank. (Tribune Dhaka,11July 2018) |
| Janata Bank (2010-2015 & 2013 to present Janata Bank, Prime Bank, Jamuna Bank, Shahjalal Islami Bank Ltd and Premier Bank (June2011-July2012) AB Bank (2013-2014) |
Deceit by Crescent and Anon Tex involving BDT 10, 000crores. (DhakaTribune,3rd November 2018) Concealing of BDT1,174.46 by Bismillah Group and its fake sister concerns. (The Daily Star,7th October 2016) |
A panel of investigation, headed by a BB Executive Director, presented a report on the scam to the BB on 30 October 2018. (Tribune Dhaka, 3 November 2018). The ACC lodged 12 cases over the Scam on November 3, 2013, against 54 individuals. (The Independent, September11, 2018). |
| NRB Commercial Bank (2013- 2016) | Gross anomalies over distributing loans of BDT 701crores. New Age Bangladesh,10th December 2017) | The central bank assigned an observer to restore discipline and corporate governance at the bank on December 29, 2016. (Tribune Dhaka,7th December 2017) |
| Janata Bank (2013-16) | Loan scam involving BDT 1,230 crores (The New Nation,22nd October 2018) | Thermax demanded that the entire loan be rescheduled again in October 2018 (earlier restructured in 2015). The board of Janata Bank-supported Thermax’s suggestion and sent it for approval to Bangladesh Bank. (Daily Star, October 21,2018 |
| Farmers Bank (2013-2017) | Fund theft of by 11 companies e.g.: NAR Sweaters Ltd, Advanced Development Technologies, etc. involving BDT 500 crores. (The Daily Star, 24th March 2018) |
In January 2018, the BB directed Farmers Bank to perform a functional audit on loan accounts in its Motijheel branch with an exceptional sum of at least BDT 1crore. (Daily Star,24 March 2018) In April 2018, four suspects were detained by the Anti- Corruption Commission (ACC), including the former Chairman of the Audit Committee of the Farmers Bank. (The Independent, April11,2018) |
| Bangladesh Bank (February 5, 2016) | The heist of BDT679.6 crores (USD81million) by international cyber hackers from reserves account of Bangladesh Bank with the New York's US Federal Reserve Bank. (The Daily Star, 5 th August 2017) | The government created a 3-member inquiry committee on March 19, 2016, led by former Central Bank governor Dr. Farashuddin. (Daily Star, August 5,2017) |
| Dutch Bangla Bank Limited (MayJune,2019 | Tk16 lakh stolen by the members of the international hacker group. They used Tyupkin Malware to make the ATM infected and to stop all network connections and there is no record of the transactions. (The Daily Star, June11,2019) | Six Ukrainian s were detained on 1st June 2019.This problem is being investigated jointly by the Detective Branch, Counter- Terrorism and Transnational Crime Cybercrime Unit (CTTC) and CID. |
| Biman Bangladesh Airlines | Biman Bangladesh Airlines has reportedly been facing delays in the disbursement of salaries to its employees reportedly due to the cyber-attack on the national carrier's email servers in March this year. The government declared 29 organizations, including Biman, as “critical. information infrastructure” under the Digital Security Act. (TBS Report, 12 June, 2022) |
Source: Report on Banking Sector in Bangladesh, Centre for Policy Dialogue, 2018, quoted in Joveda et al., 2019
The above table -2 reveals that major embezzlement and cyber-attacks for the last few years occurred in public owned banks and few occurrences related to private sector banks. As measures: cases submission against the banks, report submission by the panel of investigation team, inquiry committee created by government and appointing observer to restore discipline and corporate governance etc. have been presented in the above table.
Table 3: Total Money Lost through Major Scams, Irregularities, & Heists as reported in the media.
| Sonali, Janata, NCC, Mercantile & Dhaka Bank | BDT 4.89 crore |
| BASIC Bank BDT 4,500 crore | BDT 4,500 crore |
| Sonali Bank BDT 3,547 crore | BDT 3,547 crore |
| Janata Bank BDT 10,000 crore | BDT 10,000 crore |
| Janata Bank, Prime Bank, Jamuna Bank, Shahjalal Islami Bank & Premier Bank | BDT 1,174 crore |
| AB Bank | BDT 165 crore |
| NRB Commercial Bank | BDT 701 crore |
| Janata Bank | BDT 1,230 crore |
| The Farmers Bank | BDT 500 crore |
| Bangladesh Bank | BDT 679 crore |
| TOTAL | 22,501 crores |
| USD | (USD 2.68 billion) |
4.6 Provisions and Laws:
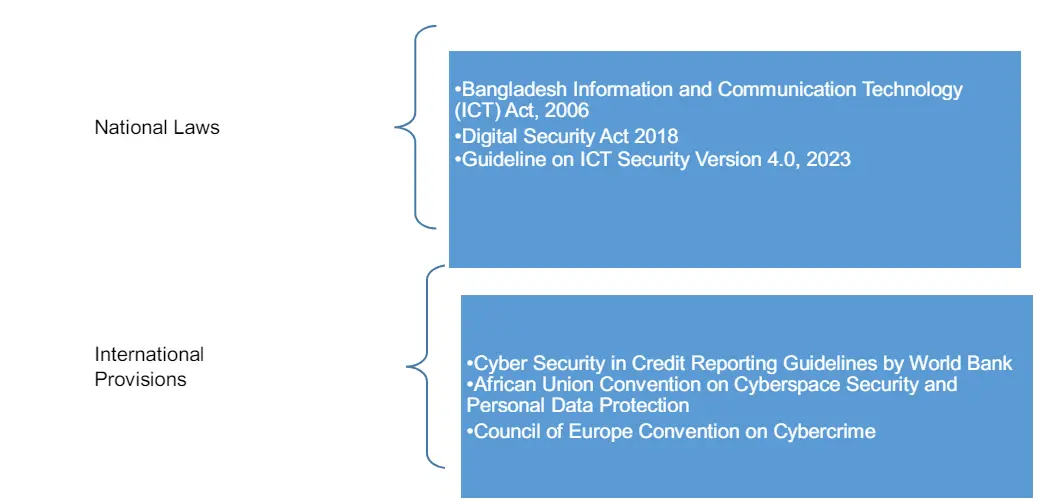
4.6.1 National Laws:
4.6.2 International Provisions:
2. CONCLUSION & RECOMMANDATIONS:
In this article after attempting to define cyber-crime, we examine the problems that have played a major role in increasing financial cyber-crime in Bangladesh. We will also examine the loopholes in cyber laws related to financial organizations existing in Bangladesh to combat economical cybercrimes. We also look at the challenges of identifying and quantifying the ratio of economic cybercrime, the approaches taken to try and punish or prevent it, and the efficacy of these measures. The main aim of this paper will be to propose some guidelines for the financial sectors to protect their data and other valuables in reference to the law practices in other developed countries.
3. REFERENCES:
Information on http://www.asianlaws.orgiccyberlawlibrary/cc/what_cc.htm “
Cybercrime: The Growing Threat to Global Banking”
(https://internationalbanker.com/banking/cybercrime-growing-threat-global-banking/).
Information on http://www.asianlaws.orgiccyberlawlibrary/cc/what_cc.htm
Information on https://swivelsecure.com/solutions/banking-finance/5-cybersecurity-weaknesses-threatsinbanking-and-financeindustry/).
Information on https://www.unodc.org/unodc/en/cybercrime/global-programme-cybercrime.html).
Information on http://www.asianlaws.orgiccyberlawlibrary/cc/what_cc.htm
Information on http://worldofscience.com.my/aboutchemistry.html
Information on www.computingbasic.com.html
Information on https://www.researchgate.net/publication/353443653